We all get spam. These unsolicited emails are mostly just annoying, but some spam is dangerous, luring us to turn over passwords or financial information. It’s easy to fall for a convincing “phishing” message – they’re designed to trick you. Security tools alone can’t protect you from these quickly changing social engineering techniques. Here’s what you need to know to stay safe.
What are the dangers of spam?
An unsolicited (or “spam”) email has the potential to:
- infect your computer with a virus
- install spyware or adware to watch your actions online
- “phish” you into providing personal information on a web site or return e-mail
- steal personal information from your computer
How Do I Know If I Have Malware?
Malware, short for malicious software, is software designed to disrupt computer operation, gather sensitive information, or gain unauthorized access to a computer system.
COMMON TYPES OF MALWARE
Viruses: Viruses are destructive programs that may slow performance, cause data corruption/loss, or reboot your system unexpectedly.
Ransomware: Ransomware is a specific kind of virus that locks the hard drive of a computer (and in rare cases, a phone). Cyber criminals then extort payment ($25-$5000) in exchange for unlocking it. If payment isn’t made, they erase all the files and in some cases, disable or damage the operating system. Common forms of ransomware include Cryptolocker, Cryptowall, TeslaCrypt and 7ev3n.
Adware and Spyware: Adware is malicious software that downloads or displays unwanted advertisements. These advertisements are usually integrated into free software programs that a user downloads. Spyware specifically tricks a user to install a program that gains information such as passwords, bank information, and other valuable data without the user’s consent.
HOW TO AVOID MALWARE
Viruses: Viruses are most commonly spread by means of e-mail (generally via infected attachments or links to infected websites), rogue instant messenger links, or exploitations of unpatched Windows computers. If an email looks suspicious to you, do not open links or attachments in it.
Ransomware: Just like other viruses, a computer can be infected from clicking a malicious link in an email attachment or downloading a malicious file. A phone can be at risk from malicious apps. Think before clicking on links or downloading apps. Hover over links on your computer to make sure the link is actually pointing to where it should be. On iPhones and Androids, you can “press and hold” the link to reveal the actual target address for you to assess. If the link is not going where you expected, don’t click it. Also, keep your devices updated: Having the most current versions of software (especially anti-virus) and operating systems keeps your machine safer.
Adware and Spyware: Stay away from torrent applications and sites that offer streaming and downloading of movies at no cost. Only use trusted sources to download free software, other malicious sites may give you software that has spyware wrapped in it as a “bonus.” Some web pages will also install Spyware in the form of “cookies” when you surf onto the site, so be sure you are only visiting reliable sites.
HOW TO REMOVE EXISTING MALWARE
Be sure that your machine (Mac or Windows device) is running trusted antivirus software. If your issue persists please visit the Help Desk for Service.
10 tips for escaping internet phishers
- Delete e-mails from unknown senders
- Only open expected attachments from people you know
- Never respond to a spam (clicking on “please remove me from your mailing list” links may result in more spam)
- Treat your e-mail address like a credit card number – never submit it to a person or site you do not trust
- Never make a purchase from a spam message
- Do not click links from commercial e-mails even if you trust the company; phishers can mask malicious content to look convincing from trusted sources – even the IRS!
- Do not provide your e-mail on public forums or web sites
- Do not give out your name, SSN, telephone number, street address, birth date, credit card numbers, driver’s license number, or vehicle registration plate number via e-mail
- Keep your antivirus software and operating system current to fix and prevent vulnerabilities that spam or attachments could exploit
- Regularly check your free credit report at https://www.annualcreditreport.com/cra/index.jsp
Examples of spam phishing messages
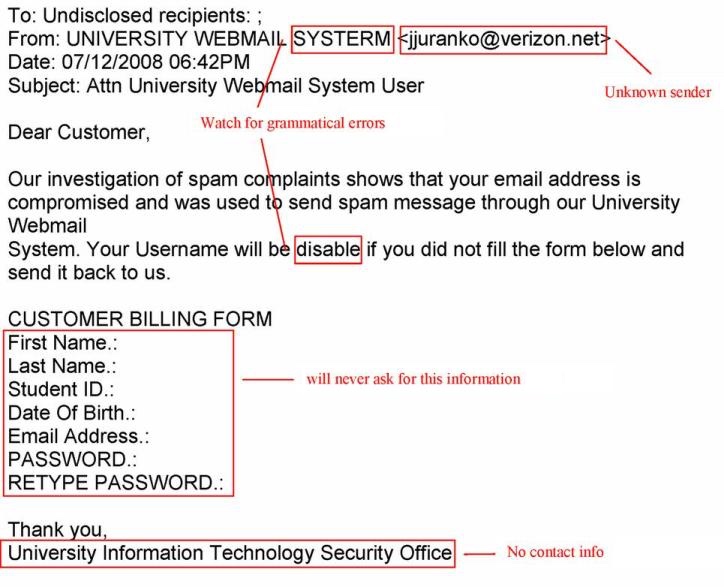
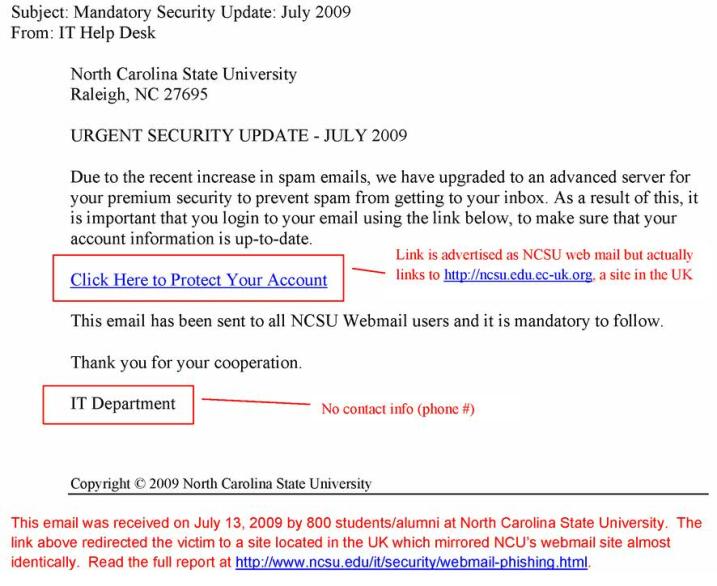
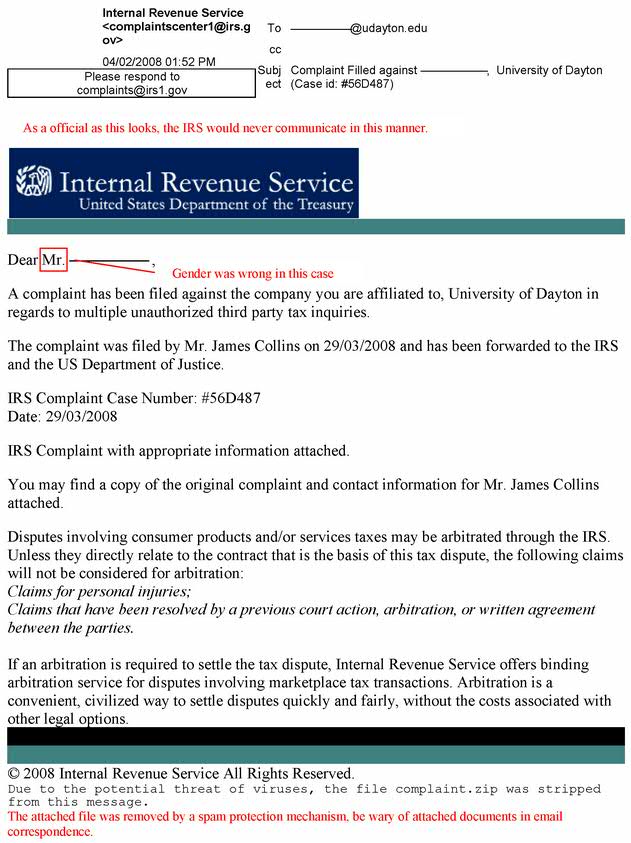
CAN YOU SPOT THE PROBLEMS?
This is an example of a SPAM message intended to “phish” for a username and password.

Notice these red flags:
- This email is not addressed to anyone in particular.
- It neither carries a name nor an eBay login name.
- Also note the threat of account suspension if you do not act quickly.
If questioning the validity of a message like this (after all, you might well be an eBay account holder), it’s best to load the eBay.com web site in a fresh browser window instead of clicking on a link from an email to put all fears to rest.
Reporting phishing, scams, or other attempts to defraud
Reporting to IT&S
You can report phishing and phone scams to [email protected] . Knowing about scam attempts allows IT&S to notify campus if necessary.
Reporting to Gmail
You can protect others outside of Chaminade from scam emails, too. From your Chaminade Gmail, click the “Report Phishing” option under the message reply options. If several users report a particular message, Google will begin blocking it.

Think you’ve been hacked?
- If you believe you might have revealed sensitive information about your organization, report it to the appropriate people within the organization, including network administrators. They can be alert for any suspicious or unusual activity.
- If you believe your financial accounts may be compromised, contact your financial institution immediately and close any accounts that may have been compromised. Watch for any unexplainable charges to your account.
- Contact the Federal Trade Commission’s ID Theft Clearinghouse. Phone: 877-438-4338, TDD 202-326-2502
- Report the problem to law enforcement agencies through NCL’s Fraud Center.
Remember: IT&S will never ask for personal information via e-mail.
Resources
Learn more about phishing and spam at these Websites:




